Securing the root user on macOS High Sierra
Photo by Luca Bravo on Unsplash
Update: Apple has released an update that fixes this security vulnerability. See https://support.apple.com/en-us/HT208315 for more information.
A developer in Turkey recently tweeted about a significant security vulnerability in macOS High Sierra
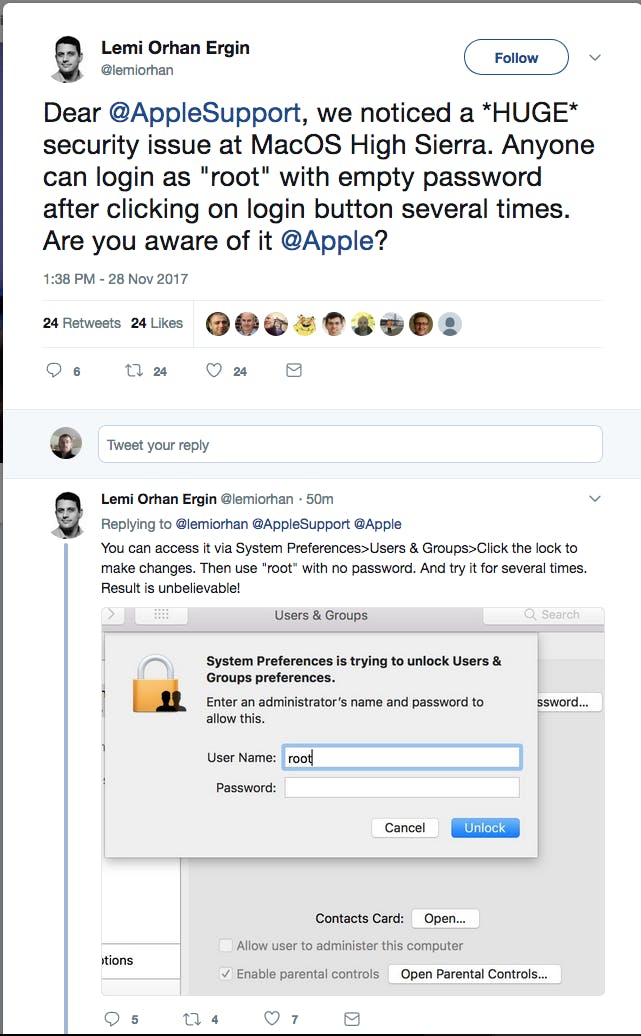
For those who don’t know, the “root” user exists on all Mac and Linux boxes and is the ultimate super user. There’s nothing that root cannot do. Getting access to the root user is considered the ultimate goal when trying to compromise a computer, whether that’s locally or remotely through the Internet or local intranet. Getting unauthorized access to the root user is a bad, bad thing.
As such, our first thought was no, that can’t possible be true, but sure enough it was as trivially reproducible given the steps provided in the tweet. Even worse, it’s possible to sign in as root from the login screen with no password whatsoever (you’ll end up logged in as “System Administrator”)! How could such a thing happen?
Well I don’t have an answer for how but we were able to figure out what is happening. By default the root account is supposed to be disabled, but by default the root user also has a blank password. For some reason, the system is first enabling the root user (which is supposed to be disabled by default) then doing a password check. With no set password, submitting a blank password matches and you’re in.
There is an easy fix: set the root user’s password. There are two ways of going about this, the command line via Terminal, iTerm, and the like, or through the Directory Utility tool.
On the command line, you can set your computer’s root password thus:
sudo passwd -u rootThis will first ask you for your current account password (as with any use of sudo or an installer). Then you’ll be asked to enter a new password twice.
Alternatively, in Directory Utility, you’ll need to unlock administrator changes (which can be done with “root” and no password here too!):
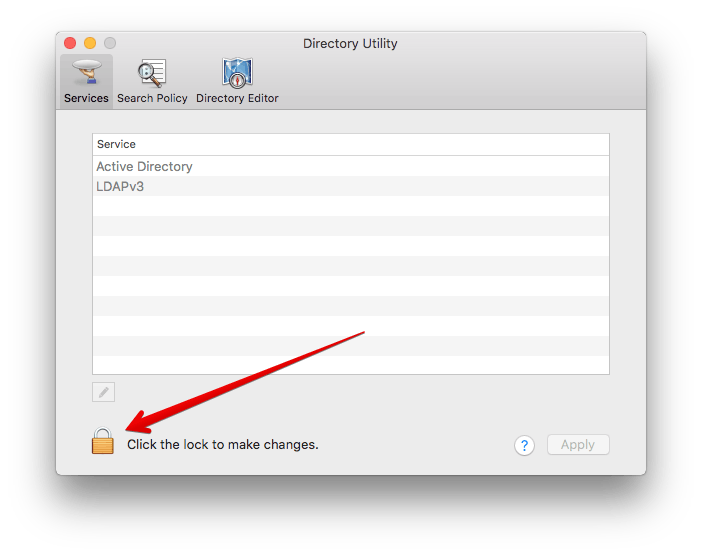
Once unlocked, go to Edit and Change Root Password. Enter in the new password twice.
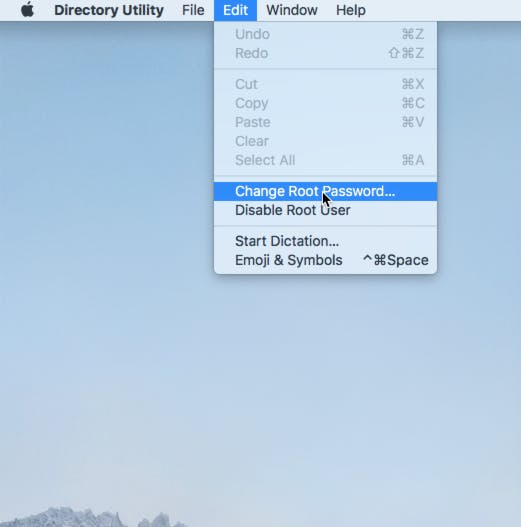
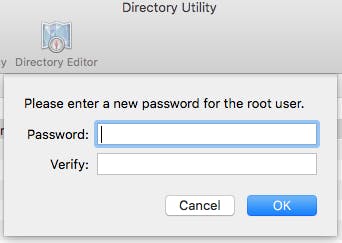
Disabling the root account will not close this hole because the system insists on re-enabling the account as soon as a log in as “root” is attempted.
With an explicit password set, you’re now protected against this vulnerability.

Comments
Have you informed Apple through the proper security disclosure channels? Not great practise to broadcast this to the world before giving them a chance to fix it.
Paul: I agree with you that blasting this across Twitter was not the best way of disclosing this issue. However, we did not originally disclose this bug. Once the tweet went live, the window for responsible disclosure unfortunately ended. With that, I am just providing information here on how to fix your machine before Apple gets a fix in themselves.
This article is useful to each and every Mac user. I’m thankful for that.
This article is useful to each and every Mac user. I’m thankful for that.
How to Protect the root user on macOS High Sierra you share is quite meticulous and easy to understand. I will install it shortly. thank you very much.
temple run